PGP Encryption
October 09, 2016
A few weeks ago I gave a talk on a piece of technology that I personally am fascinated with, PGP encryption. To anyone who is new to this type of encryption, or to cryptography as a whole, here are my slides and talking points.
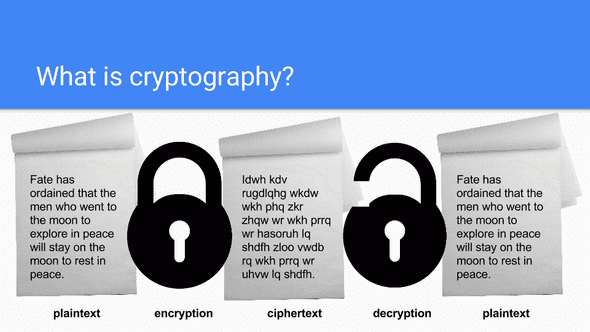
So what is cryptography? Cryptography is the science of using mathematics to encrypt and decrypt data. This is especially useful when that data needs to be transmitted over insecure networks, such as the internet.
In order to encrypt data, you must first apply a cryptographic algorithm (mathematical function) to it, also known as a cipher. This cipher typically will have one input (a key) which is used in both the encryption and decryption process.
In the end, the security of your data is entirely dependent on two things: the strength of your cipher and the secrecy of your key.
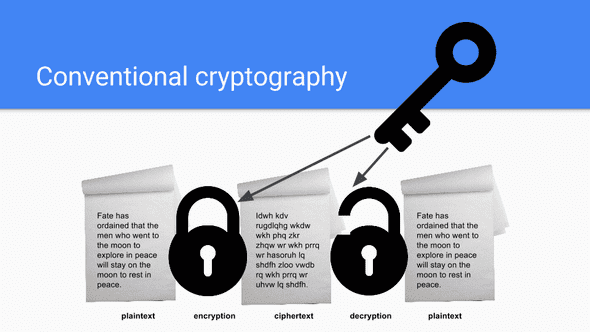
In what is referred to as “conventional cryptography” one key is used for both the encryption and decryption process. This type of cryptography is also known as secret-key or symmetric-key encryption. In Hollywood, you’ve probably seen a spy movie or two where the secret agent has a briefcase locked to their wrists. That briefcase likely contains a secret key that the agent will die trying to protect. Again, the strength of this encryption almost entirely depends on the ability for the agent to keep that briefcase secured from his/her enemies. That is why this type of encryption is losing popularity in modern times - especially if you consider that Julius Caesar himself used it over 2,000 years ago.
If you’re a software engineer, you’ve probably encountered a Caesar’s Cipher coding challenge before. For those that haven’t, let me explain the concept. When Caesar wanted to send messages to his generals, he didn’t have the luxury of WhatsApp and their built-in Curve25519 encryption. No, he had to write his messages down and ask a messenger to deliver them.
Unfortunately, a man of power such as his entitled him to an equal amount of enemies. As such, Caesar devised of a plan so that his messages would mean nothing if they ended up falling into the wrong hands. That plan was to shift all letters in the alphabet up by three letters, better known as “shift by 3”. This way, only those who knew the “shift by 3” rule could decode his messages.
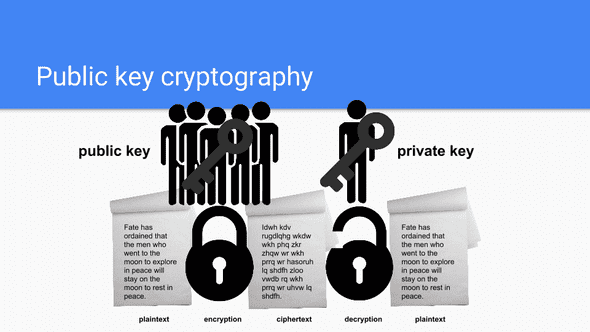
How can modern technology solve for inherit security holes caused by conventional cryptography? One way is with public key cryptography. This type of cryptography uses a pair of keys for encryption. One key is public and is in charge of the encryption process. The other is a private key which corresponds to the public key and handles the decryption process. In this form of encryption, one publishes their public key for anyone and everyone to see. But, any message encrypted with that public key can only be decrypted by the holder of the public key. This enables secure communication between parties without any need to previously disclose a secret key with one another.
A popular example of this encryption technique that you may have used without even realizing it is RSA.
And this finally brings us to PGP encryption. PGP, short for Pretty Good Privacy, combines some of the best features of both conventional and public key cryptography - it is lovingly known as a hybrid cryptosystem.
Just like in public key cryptography, users share their public keys and keep their private keys private. But, PGP has a few advantages over traditional public key encryption.
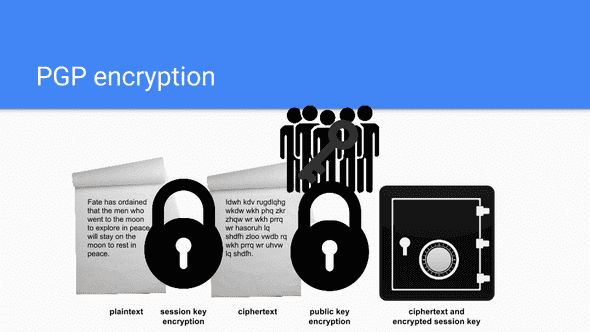
First, the data is compressed. Compression will not only save on disk space and reduce transfer times, but also can strengthen the encryption. When a hacker tried to crack an encrypted message, they’ll often utilize exploits that search for patterns in the raw data. Compression makes these patterns even harder for a computer to identify.
Next, PGP will create a session key, which is effectively a temporary secret key that will only be used once. This session key is created from the movements of the encryptor’s mouse and their keystrokes. At this point, the data is encrypted with that secret key using conventional techniques - benefitting from a fast and secure algorithm.
Once the data has been encrypted, the session key is then also encrypted to the recipient’s public key. The data and the session key are then wrapped up together and transmitted to the recipient for decoding, which essentially reverses this process.
If you want to give PGP encryption a try, check out these easy to use online encryption and decryption tools. But, once you’re ready to actively use PGP encryption for your communication needs though, you should not use an online service as you don’t have full control and ownership of your session keys and never really know what data is being transmitted behind the scenes. For those that want to dive deeper into secure PGP technologies, check out GPGTools.
Want to learn more about encryption? Khan Academy has a great introductory series called Journey into Cryptography. There, you’ll learn about a wide variety of encryption techniques and technologies, including the one-time pad. I personally became interested in one-time pad encryption after hearing a fascinating story about encryption techniques used during World War II. To hear more about that story, check out the Vox Ex Machina episode from one of my personal favorite podcasts, 99% Invisible.